SUPERNOVA
Following the discovery of SUNBURST, a separate, unrelated security threat was discovered and made public – a backdoor that is being referred to as SUPERNOVA. The SUPERNOVA6 malware, characterized as a web shell, was deployed by targeting a vulnerability7 in specific versions of the SolarWinds Orion product that has since been patched.
It is important to note that SUPERNOVA is not associated with the supply chain attack used to distribute the SUNBURST backdoor. SUPERNOVA was neither signed nor delivered by SolarWinds.
Conclusion
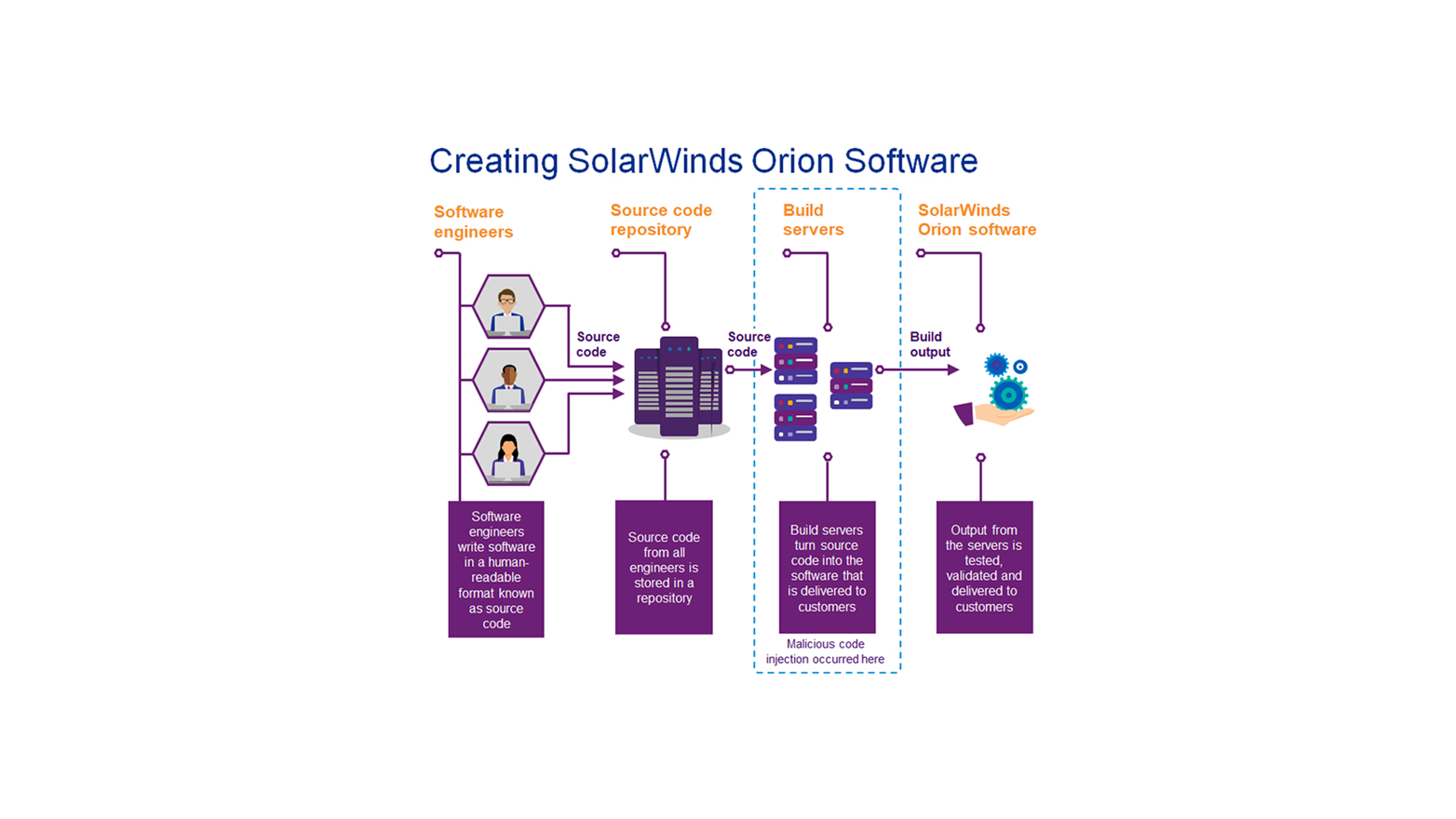
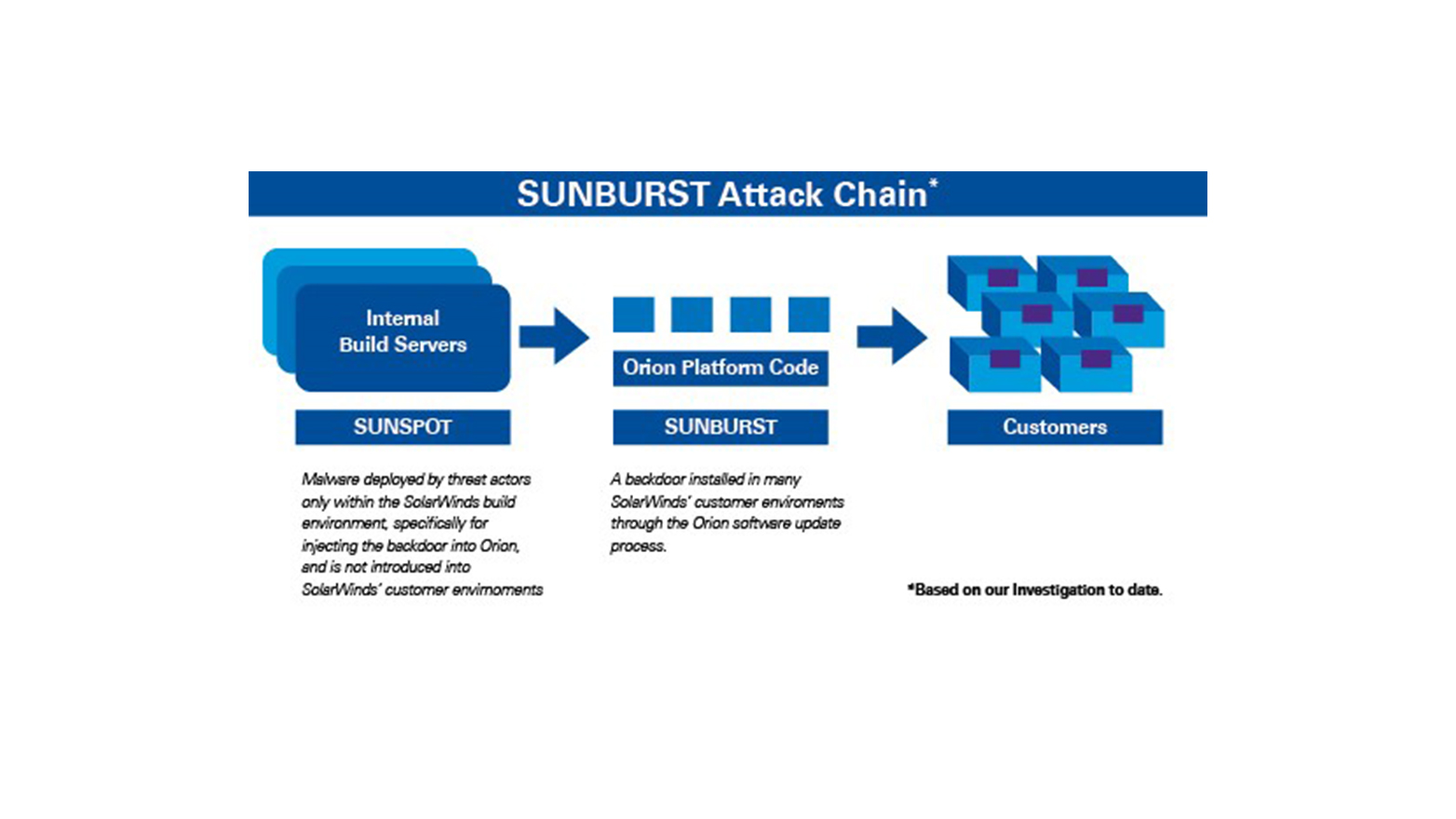
In summary, SUNSPOT was designed by the threat actor(s) to function specifically within SolarWinds’ software build environment to insert a malicious backdoor called SUNBURST into certain versions of the SolarWinds Orion Platform software. Unlike the SUNBURST backdoor, SUNSPOT was not included in the SolarWinds Orion Platform software patches that were made available to the public.
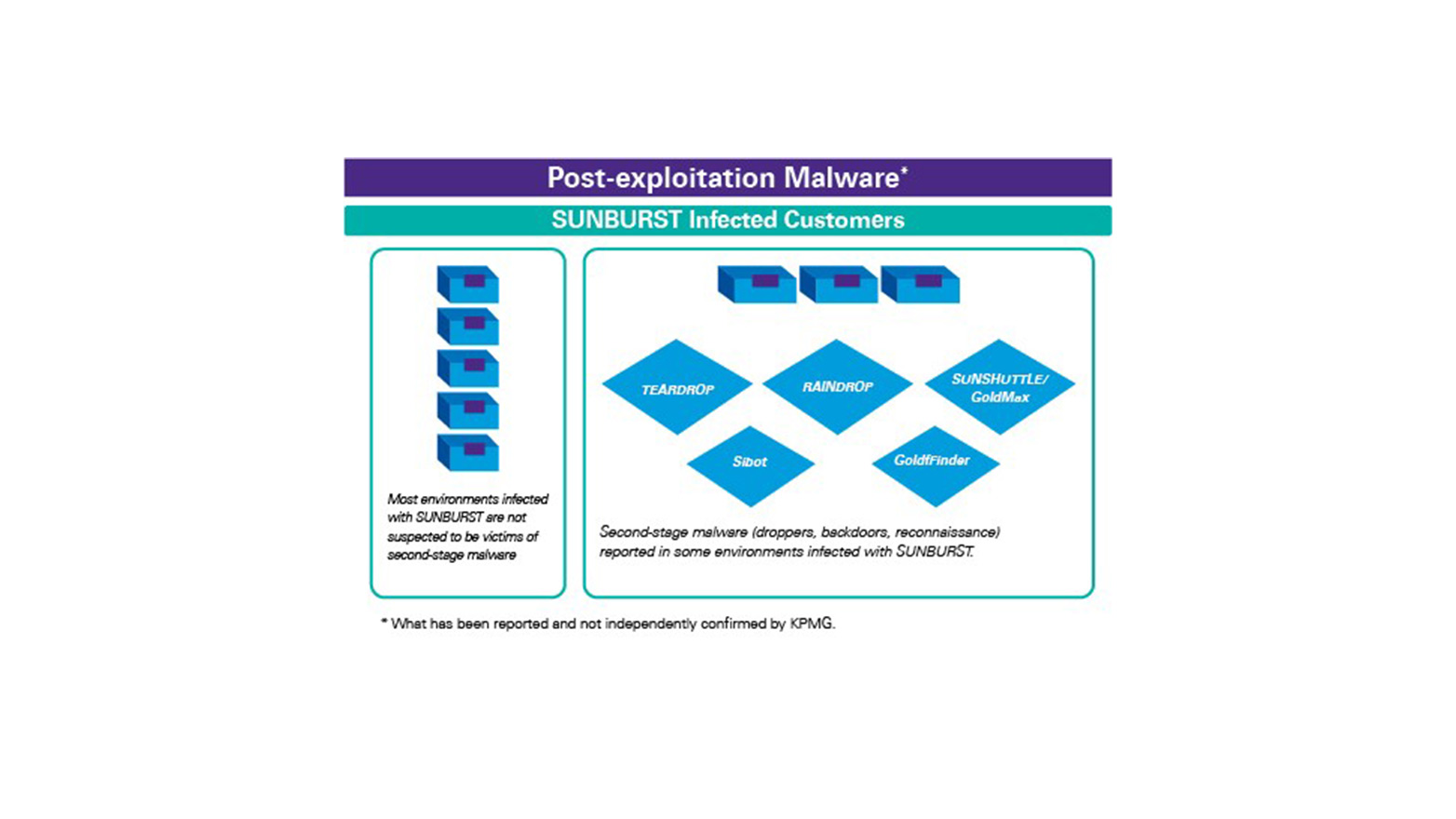
As reported TEARDROP and RAINDROP were designed to be used by the threat actor(s) to deploy a modified version of Cobalt Strike. Further, SUNSHUTTLE/GoldMax, GoldFinder, and Sibot are malicious tools reported to have been used by threat actor(s) in an environment where there was a pre-existing SUNBURST compromise.
Like SUNSPOT, neither TEARDROP, RAINDROP, SUNSHUTTLE/GoldMax, GoldFinder, nor Sibot were included in SolarWinds Orion Platform software or directly provided to customers through SolarWinds patches. Finally, while still relevant, the backdoor web shell SUPERNOVA, identified after the SUNBURST attack was made public, is not associated with the SUNBURST supply chain attack and was not included in any SolarWinds Orion Platform software patches.
| Malware | Distributed by
SolarWinds | Type of Malware |
|---|
| SUNSPOT | No | Code injector |
| SUNBURST | Yes | Backdoor |
| TEARDROP | No | Dropper |
| RAINDROP | No | Dropper |
| SUNSHUTTLE/ GoldMax | No | Backdoor |
| GoldFinder | No | Reconnaissance |
| Sibot | No | Backdoor |
| SUPERNOVA | No | Backdoor |
Future KPMG posts will outline how to identify similar attacks, demonstrate how the malware was found, and illustrate lessons learned and KPMG’s secure by design leading practices.
Special recognition of the KPMG Cyber Security professionals contributing to this blog include Andi Baritchi, Stephen Gibson, and Christopher Shanahan.